-
Blog Post Dec 18, 2019
Sectigo Executives Share 2020 Predictions
Turning attention to 2020, our leadership team has been working to identify predictions about quantum computing, automation, IoT security, and legislation.
-
Press Release Dec 18, 2019
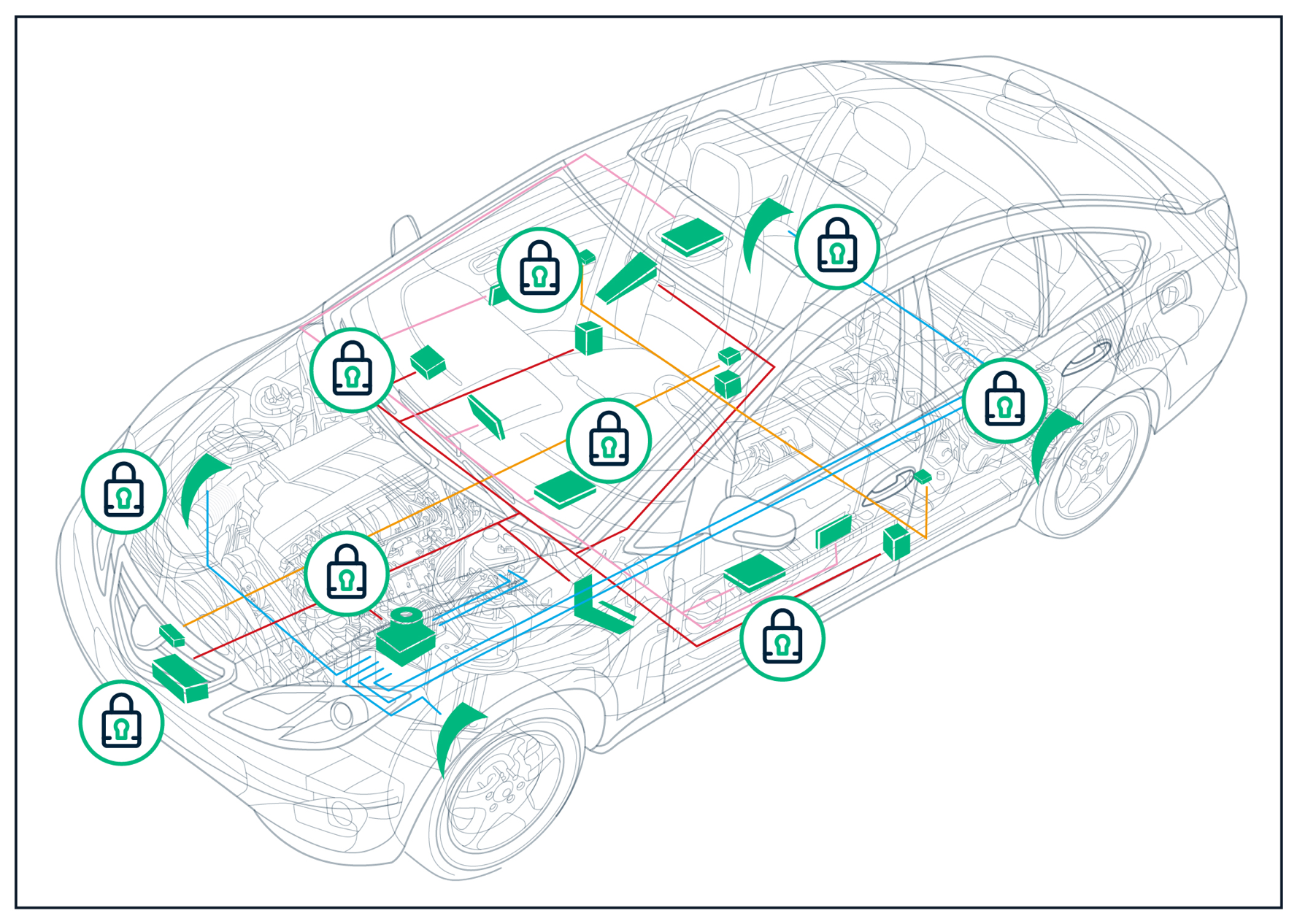
Sectigo Releases Embedded Firewall to Protect Automotive Systems
Sectigo released the Sectigo Embedded Firewall for Automotive to better protect vehicles from cyberattacks. Mentor, a Siemens business, has integrated the Sectigo Embedded Firewall for Automotive with its popular AUTOSAR platform and a global tier-one automotive ECU supplier is among the early adopters the Sectigo-enabled AUTOSAR platform, indicating the urgency for embedded security.
-
Learn More
Keeping Medical Devices, Services, and Data, Safe from CyberAttacks
A News Article from Sectigo
 News Article Dec 18, 2019
News Article Dec 18, 2019In the last few years, hospitals and medical facilities have been successfully targeted by cyber crooks looking to exploit or wreak havoc on the healthcare sector and its patients. Emboldened by the industry’s slow progress in adopting technologies that harden medical devices and data systems, criminals have upped their game.
-
Learn More
Failure to Secure IoT Networks Has Far-Reaching Consequences...
A News Article from Sectigo
 News Article Dec 10, 2019
News Article Dec 10, 2019Transportation is rated by Gallagher as the third-most-vulnerable industry to cyberattack, and as partially or fully autonomous vehicles continue to hit the market, the potential consequences of an attack grow more serious.
-
Listen Now

EPISODE 55
Broadcast Date:
December 5, 201922 minutes
 Podcast Dec 05, 2019
Podcast Dec 05, 2019Root Causes 55: California's New IoT Security Law
California Senate Bill 327 makes device security a requirement in California, setting the precedent for IoT security practices. Join us to learn more.
-
Blog Post Dec 04, 2019
Five Ways PKI Protects and Secures Financial Services Data
Data has become the lifeblood of the financial services industry. From managing transaction details and providing real-time account and trading information to automating risk management processes, forecasting, and fraud detection, data is integral and the most important resource to protect.
-
Learn More
Connected Cars Need Stronger Identity for Safer Streets
A News Article from Sectigo
 News Article Dec 03, 2019
News Article Dec 03, 2019When “devices” are vehicles transporting people at high speeds on roadways, these vulnerabilities become safety risks. Embedded firewalls maximise driver safety and help prevent the loss of intellectual property, disruption of services, and proliferation of an attack to other systems.
-
Listen Now

EPISODE 54
Broadcast Date:
December 2, 201925 minutes
 Podcast Dec 02, 2019
Podcast Dec 02, 2019Root Causes 54: 2019 Lookback - Infrastructure and IoT Security
It was an eventful year for infrastructure and IoT security. Join our hosts as they discuss 2019 trends and 2020 predictions for IoT and infrastructure.
-
Blog Post Nov 20, 2019
Australia's IoT Cybersecurity Guidelines for Embedded Device Security
Australia has joined the ever-swelling ranks of government and industry organizations developing guidelines or enacting regulations regarding IoT device security. On Nov. 11, 2019, the country published their “Draft Code of Practice: Securing the Internet of Things for Consumers,” which outlines 13 security practices intended to apply to all IoT devices available in Australia.
-
Download Now
Sectigo IoT Use Case: Private PKI for Manufacturing
A Datasheet from Sectigo
 Datasheet Nov 18, 2019
Datasheet Nov 18, 2019To enable secure authentication and prevent counterfeiting, OEMs and manufacturers add certificates to their IoT devices and chips at the assembly line.
-
Watch Now
2 minutes
Product Video Nov 14, 2019Augment Microsoft CA and Secure Non-Windows Devices and Applications
Sectigo Certificate Manager can augment Microsoft CA to secure non-Windows applications, mobile devices, web servers, IoT, DevOps, SSH, and more.
-
Download Now
IoT Identity Platform
A Datasheet from Sectigo
 Datasheet Nov 11, 2019
Datasheet Nov 11, 2019The Sectigo IoT Identity Platform removes complexity associated with securing and authenticating connected devices, so you can protect your infrastructure.