What is an X.509 certificate and how does it work?


An X.509 certificate is a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, which defines the format of public key infrastructure (PKI) certificates. They are used to manage identity and security in internet communications and computer networking. They are unobtrusive and ubiquitous, and we encounter them every day when using websites, mobile apps, online documents, and connected devices.

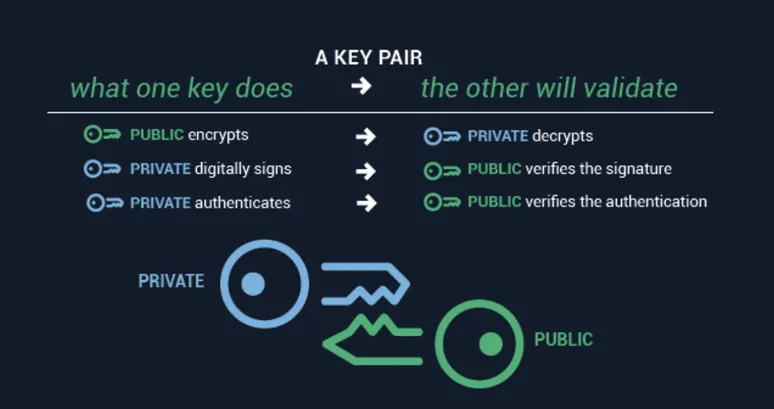
One of the structural strengths of the X.509 certificate is that it is architected using a key pair consisting of a related public key and a private key. Applied to cryptography, the public and private key pair is used to encrypt and decrypt a message, ensuring both the identity of the sender and the security of the message itself. The most common use case of X.509-based PKI is Transport Layer Security (TLS)/Secure Socket Layer (SSL), which is the basis of the HTTPS protocol, which enables secure web browsing. But the X.509 protocol is also applied to code signing for application security, digital signatures, and other critical internet protocols.
Version history
The first version of the X.509 standard was published back in 1988. Looking to formalize the rules for certificate issuance, the Telecommunication Standardization Sector of the ITU (ITU-T) developed a hierarchical system for distinguished names that followed the electronic directory service rules for X.500 and was inspired by the systems used to assign telephone numbers globally but applied to the more flexible organizational requirements of the Internet.
In 1996, version 3 of the standard provided a major update with the addition of multiple extensions that are still used today to support the expansion and new applications of internet use.
Now version 9 is the current version of the standard, having been defined in October 2019.
Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280).
The benefits of X.509 certificates
As X.509 certificates facilitate secure messaging and web browsing, there are significant benefits for organizations to use them.
Establish Trust
Digital certificates, also known as public key certificates, allow individuals, organizations, and even devices to establish trust in the digital world. As the foundation for all digital identities, X.509 certificates are everywhere and are essential to every connected process from websites to applications to endpoint devices and online documents. For example, without these, we wouldn't be able to trust that www.amazon.com is actually Amazon's website.
This level of trust is established both by how X.509 certificates work and by how they are issued. The key usage architecture lets certificates verify that:
A public key belongs to the hostname/domain, organization, or individual contained within the certificate
It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed.
When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance.
Enable scalability
An additional benefit of this certificate-based approach to identity is scalability. The PKI architecture is so scalable that it can secure billions of messages exchanged daily by organizations over their own networks and across the internet. What enables this is that public keys can be distributed widely and openly without malicious actors being able to discover the private key required to decrypt the message.
How do X.509 certificates work?
The X.509 standard is based on an interface description language known as Abstract Syntax Notation One (ASN.1), which defines data structures that can be serialized and deserialized in a cross-platform way. Leveraging ASN, the X.509 certificate format uses a related public and private key pair to encrypt and decrypt a message.
The basis of public key infrastructure
The public key consists of a string of random numbers and can be used to encrypt a message. Only the intended recipient can decipher and read this encrypted message and it can only be deciphered and read by using the associated private key, which is also made of a long string of random numbers. This private key is secret and is known only to the recipient. As the public key is published for all the world to see, public keys are created using a complex cryptographic algorithm to pair them with an associated private key by generating random numeric combinations of varying lengths so that they cannot be exploited through a brute force attack. The most common algorithms used to generate public keys are:
- Rivest–Shamir–Adleman (RSA)
- Elliptic curve cryptography (ECC)
- Digital signature algorithm (DSA)
The key size or bit length of public keys determines the strength of protection. For example, 2048-bit RSA keys are often employed in SSL certificates, digital signatures, and other digital certificates. This key length offers sufficient cryptographic security to keep hackers from cracking the algorithm. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes.
Figure: X.509 certificates use a related public and private key pair for identity authentication and security for internet communications and computer networking
Issuance fields
X.509 certificate fields contain information about the identity that the certificate is issued to as well as the identity of the issuer CA. The standard fields include:
Version – the X.509 version that applies to the certificate
Serial number – the unique serial number identifier provided by the CA that distinguishes the certificate from others
Algorithm information – the cryptographic algorithm used by the issuer to sign the certificate
Issuer distinguished name – the name of the CA issuing the certificate
Validity period of the certificate – the start/end date and time it's valid and can be trusted
Subject distinguished name – the name of the identity the certificate is issued to
Subject public key information – the public key associated with the identity
Figure: X.509 certificates use a related public and private key pair for identity authentication and security for internet communications and computer networking
Common digital certificate extensions
In addition to its standard information fields, the X.509 version 3 defined multiple extensions aimed at supporting expanded ways client applications can use the internet. Two common X.509 certificate extensions in use today are Subject Alternative Name and Key Usage.
The Subject Alternative Name extension allows other identities to also be associated with a certificate's public key. This could include other domains, DNS names, email addresses, and IP addresses. Based on this extension, multiple-domain certificates offered by CAs are frequently referred to as SAN certificates.
Key Usage limits the use of the keys to particular purposes such as "signing-only."
Digital certificates apply hierarchical trust chains
To further establish the trust of an identity, multiple digital certificates are often combined to build a hierarchical chain of trust that provides a series of verification layers. As previously mentioned, each must be signed by an issuer CA as part of the X.509 verification process. The CA is named and stored in the root of the certificate. Additional intermediate certificates can be included in the trust chain and must be validated.
For example, when a web browser client reads the certificate, it must be able to follow the hierarchical path of certification including any intermediates required for validation that are recursively linked back to the root CA listed in the client's trust store, resulting in a complete chain of trust.
Figure: SSL/TLS certificates often combine intermediate CA certificates to create a hierarchical trust chain
Certificate Revocation Lists (CRLs)
The X.509 standard also defines the use of a certificate revocation list, which identifies all of the digital certificates that have been revoked by the issuing CA prior to the scheduled expiration date.
These revoked certificates should no longer be trusted.
CRLs offer a simple way to distribute information about these invalid certificates. However, their use is increasingly deprecated by popular web browsers and clients in favor of the Online Certificate Status Protocol (OCSP) and OCSP stapling, which offer complete revocation features.
PKI certificate encoding
One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files.
There are two encoding schemas commonly used to store digital certificates in files:
Distinguished Encoding Rules (DER) is most common, as the schema addresses most data objects. Certificates encoded by DER are binary files and cannot be read by text editors but can be processed by web browsers and many client applications.
Privacy Enhanced Mail (PEM) is an encrypted email encoding schema that can be used to convert DER-encoded certificates into text files.
Common applications of X.509 public key infrastructure
Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including web server security, digital signatures and document signing, and digital identities.
Web server security with SSL/TLS certificates
PKI is the basis for the secure sockets layer (SSL) and transport layer security (TLS) protocols that are the foundation of HTTPS secure browser connections. Without SSL certificates or TLS to establish secure connections, cybercriminals could exploit the Internet or other IP networks using a variety of attack vectors, such as man-in-the-middle attacks, to intercept messages and access their contents.
Digital signatures and document signing
In addition to being used to secure messages, PKI-based certificates can be used for digital signatures and document signing.
Digital signatures are a specific type of electronic signature that leverages PKI to authenticate the identity of the signer and the integrity of the signature and the document. Digital signatures cannot be altered or duplicated in any way, as the signature is created by generating a hash, which is encrypted using a sender's private key. This cryptographic verification mathematically binds the signature to the original message to ensure that the sender is authenticated and the message itself has not been altered.
Code signing
Code Signing enables application developers to add a layer of assurance by digitally signing applications, drivers, and software programs so that end users can verify that a third party has not altered or compromised the code they receive. To verify the code is safe and trusted, these digital certificates include the software developer's signature, the company name, and timestamping.
Email certificates
S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. By encrypting/decrypting email messages and attachments and by validating identity, S/MIME email certificates assure users that emails are authentic and unmodified.
SSH keys
SSH keys are a form of X.509 certificate that provides a secure access credential used in the Secure Shell (SSH) protocol. As the SSH protocol is widely used for communication in cloud services, network environments, file transfer tools, and configuration management tools, most organizations use SSH keys to authenticate identity and protect those services from unintended use or malicious attacks. These keys not only improve security but also enable the automation of connected processes, single sign-on (SSO), and identity and access management at the scale that today's businesses require.
Digital identities
X.509 digital certificates also provide effective digital identity authentication. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. And digital identities don't have to be restricted to devices; they can also be used to authenticate people, data, or applications. Digital identity certificates based on this standard enable organizations to improve security by replacing passwords, which attackers have become increasingly adept at stealing.
How do I get an X.509 certificate?
A critical component of deploying X.509 certificates is a trusted certification authority or agent to issue certificates and publish the public keys associated with individuals' private keys. Without this trusted CA, it would be impossible for senders to know they are in fact using the correct public key associated with the recipient's private key and not the key associated with a malicious actor intending to intercept sensitive information and use it for nefarious purposes.
Trusted, third-party CAs like Sectigo act as Certificate Authorities, but many enterprises and technology providers also choose to act as their own CA. They may also decide to use self-signed certificates. Either way, the Certificate Authority must be trusted to check and vouch for the identity of all senders whose public keys they publish, ensure that those public keys are indeed associated with the private keys of the senders, and safeguard the levels of information security within their own organization to guard against malicious attack.
Managing X.509 certificates
One of the most critical aspects of x.509 certificates is effectively managing these certificates at scale using automation. Without great people, processes, and technology in place, companies are leaving themselves open to cybersecurity breaches, outages, damage to their brand, and critical infrastructure failures.
Discover how Sectigo Certificate Manager (SCM) Pro allows you to easily manage the lifecycles of public and private digital certificates. We also offer an SCM enterprise solution to secure every human and machine identity across the enterprise, all from a single platform.