200 days until 200 days: Everything you need to know about the first stepdown in maximum certificate lifespan validity


On March 15, there are exactly 200 days until the first stepdown in the move towards 47-day certificate lifespans: 200-day lifespans. This is a dramatic first move towards shorter validity periods and acts as a wake-up call for organizations that have not yet started automating their Certificate Lifecycle Management (CLM). Sectigo is here to inform, educate, and provide solutions for businesses that are ready to tackle the future of CLM.

The clock is ticking.
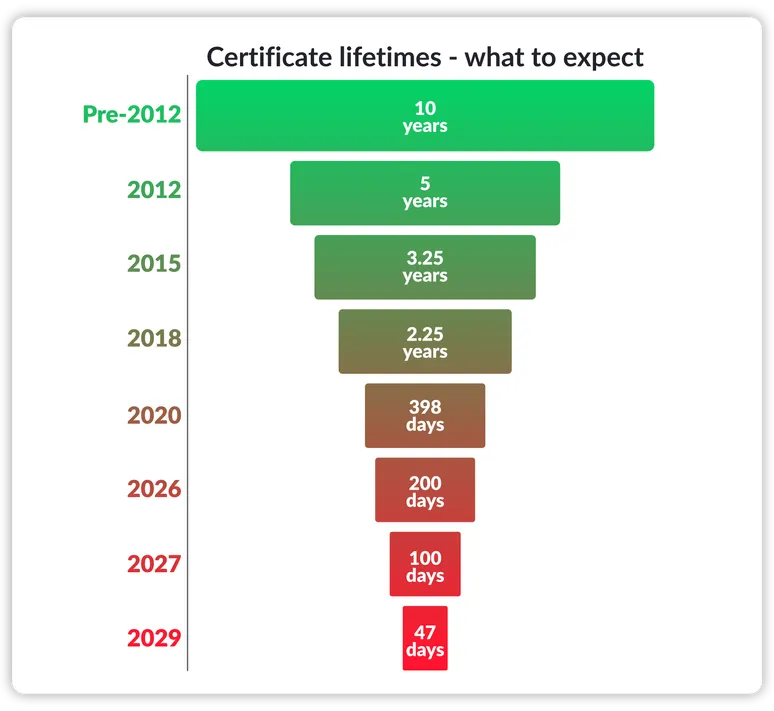
In just 200 days, the maximum SSL/TLS certificate lifespan will shrink from 398 days to 200 days, nearly a 50% reduction. This is one of the most significant changes to affect digital certificate management in over five years, and it's coming fast.
If your organization is still managing certificates manually, this shift will double your workload overnight, leaving you vulnerable to outages, compliance failures, and reputational damage. The only way to keep up? Automate your certificate lifecycle today.
What’s changing and why it matters
Right now, SSL/TLS certificates are valid for up to 398 days. But soon, you'll need to renew every 200 days.
That means:
- Twice as many renewals per year
- Half the time to act on expirations
- 2x the risk if you're relying on spreadsheets or manual processes
Shorter certificate lifespans are being pushed by major browser vendors to strengthen internet security, promote faster cryptographic agility, and limit exposure when certificates are misissued or compromised. This change in certificate validity is crucial for when postquantum cryptography (PQC) takes hold, so that organizations must stay on top of new algorithms when PQC becomes standard.
While these changes are good for the overall ecosystem and digital security, they create serious operational strain for organizations without a plan.
What the 200-day certificate lifespan means for you
Let’s break it down:
- You’ll be renewing certificates, and facing Domain Control Validation (DCV) every 6 months, instead of once a year
- The number of renewal events will double overnight
- Human error, oversight, and expired certs will become far more likely
- The risk of downtime, outages, and broken systems multiplies
This isn’t just a browser policy update, it’s a fundamental change in how the internet handles trust. And while shorter certificate lifespans improve security, they also demand real-time visibility and automated lifecycle management.
The risk of delaying automation
This is the first stepdown in a four-year shift to 47-day certificate lifespans. You may be thinking that there is time to wait, but the longer you wait to implement automation, the riskier it becomes. While 200 days may seem like a sizeable amount of time to continue with manual certificate management, it’s important to consider the implications of waiting. If you're not ready for this shift, here's what’s at stake:
- Expired certificates causing outages
Your website, APIs, and applications will go dark if certificates aren't renewed in time. - Loss of customer trust
If just one certificate misses a renewal period, this can cause a ripple effect with warnings issued on your website. Security warnings scare your users, and once trust is gone, it’s hard to win back. - Compliance failures
Regulated industries can face heavy penalties for missed renewals or insecure connections. - Burnout for IT and DevOps teams
More renewals = more manual tracking, more last-minute fixes, and more stress.
This change is happening in early 2026, but if you wait until then, it will be too late. Implementing automation takes time:
- You’ll need to discover every certificate across your environments
- You’ll need to integrate automation into your existing workflows
- You’ll need time to test and fine-tune your system before the 200-day rule becomes mandatory
Organizations that delay will face chaos: delayed renewals, missed expirations, and avoidable outages. Manual certificate management was risky at 398 days. At 200 days, it becomes unsustainable.
The ROI of automating today
Many IT organizations are reluctant to automate due to the perceived costs and complexities. While automation requires an upfront investment, the payoff speaks for itself: With native ACME support plus EST, SCEP, REST APIs, agents, and third-party automation integrations, Sectigo Certificate Management (SCM) makes certificate automation far easier than many organizations expect.
Organizations using automated Certificate Lifecycle Management (CLM) see a 3x return on investment over three years, according to a commissioned Forrester Consulting Total Economic Impact™ study of Sectigo Certificate Manager (SCM).
Here’s what automation delivers in measurable value:
- $2.6 million in productivity gains by eliminating manual certificate tracking and renewal tasks
- 60% faster certificate renewals, reducing operational risk and downtime exposure
- Up to 75% reduction in time spent on audits and compliance reporting
- Improved visibility and control over thousands of certificates across hybrid and multi-cloud environments
- Zero unplanned outages due to expired certificates, a critical savings in both financial and reputational cost
The TEI study found that SCM helps teams focus on strategic initiatives instead of certificate firefighting, while improving their overall security posture.
Bottom line: Automation doesn’t just improve security; it pays for itself.
Why awareness matters now
Certificate authorities like Sectigo are not just keeping up with these changes, they’re leading them. As an intellectual leader in the digital trust space, Sectigo is actively working to raise awareness about the 200-day shift, helping enterprises understand the urgency, the risks, and the automation solutions available.
Through ongoing industry education in the form of blogs, whitepapers, webinars, and standards committee participation, Sectigo is helping to prepare the global community before the impact of shorter certificate lifespans becomes a crisis.
Conclusion
The move to 200-day SSL/TLS certificates is one of the most urgent and disruptive changes in digital identity management today. It demands a strategic response, and that response starts with automation. Automation ensures business continuity, protects customer trust, and lets your teams focus on innovation, rather than certificate firefighting.
You now have 200 days to fix this. Don’t wait.