How Certificate Automation Secures Transport and Logistics Organizations in the 47-Day SSL Era
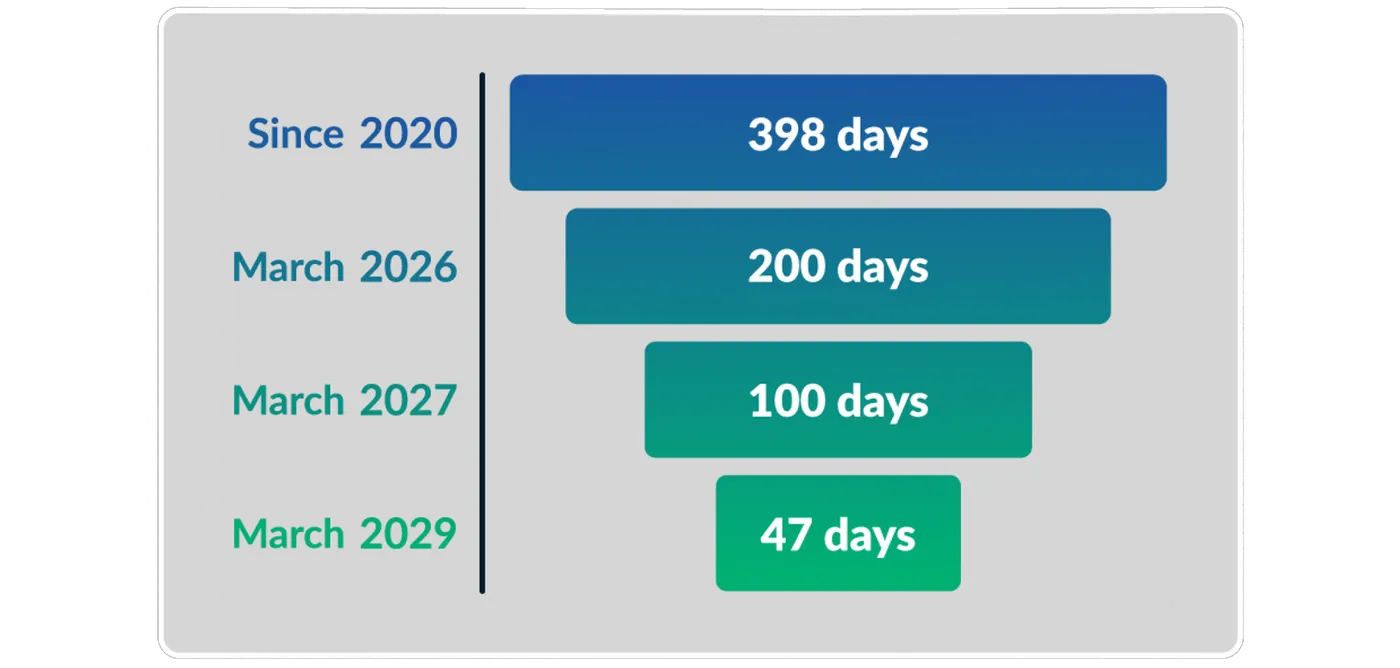
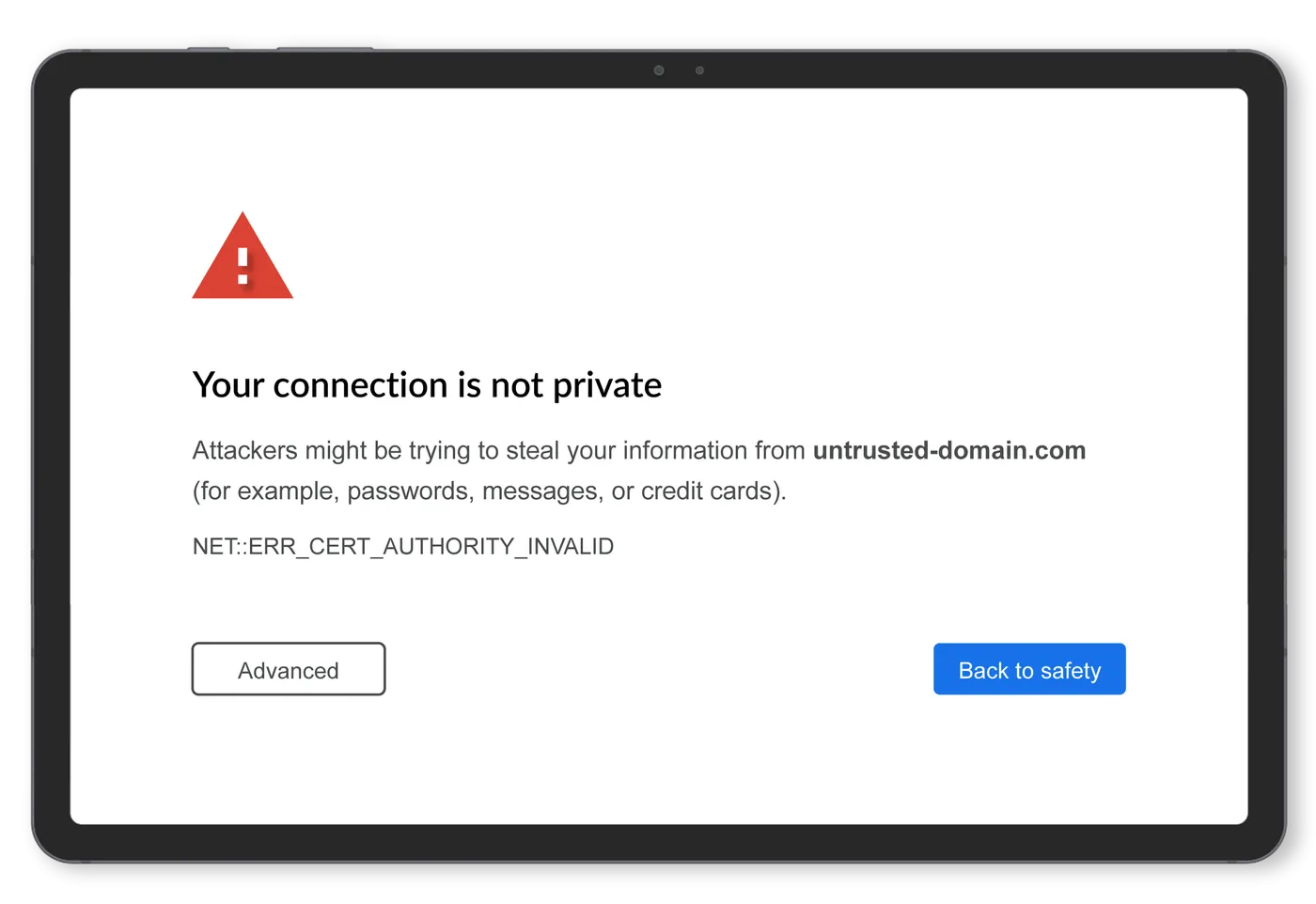
Automation is essential for transport and logistics organizations to prevent outages and secure operations as SSL certificates shrink to 47-day lifecycles.